The Register reported that two security researchers have discovered five related techniques for preemptively hijacking internet accounts.

In a paper titled "Pre-hijacked accounts: An Empirical Study of Security Failures in User Account Creation on the Web," Avinash Sudhodanan, an independent security researcher, and Andrew Paverd, a senior researcher at Microsoft, discuss their findings.
Because online services commonly fail to verify that the person signing in owns the supplied identification before authorizing usage of the account, the paper investigates how to exploit the interaction between federated identity services and traditional password-based account creation.
5 Types of Pre-Hijacking Attacks
The two researchers also wrote a blog post about their findings, describing five different types of pre-hijacking attacks.
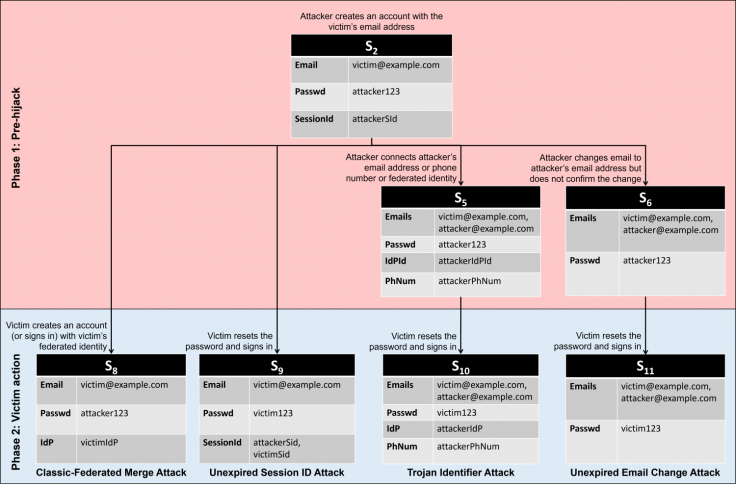
1. Classic-Federated Merge Attack: This takes advantage of a flaw in the interaction between the conventional and federated account creation processes.
2. Unexpired Session Identifier Attack: This exploits a weakness in which authenticated users are not automatically signed out of an account when they reset their password.
3. Trojan Identifier Attack: This leverages the attacker's ability to link an additional identifier to an account created through the standard username and password method.
4. Unexpired Email Change Attack: This takes use of a potential flaw in which the service fails to invalidate email-change capability URLs after a user changes their password.
5. Non-Verifying IdP Attack: This is the mirror image of the Classic-Federated Merge Attack. When creating a federated identity, the attacker uses an IdP that does not validate ownership of an email address.
The blog noted that all of these methods require the attacker to identify services where the victim does not currently have an account but is likely to create one in the future.
Almost Half of 75 Tested Popular Services Could Be Exploited via Pre-Hijacking Attacks
According to The Register, because none of these are guaranteed to work, they may appear speculative. However, they proved to be functional enough to test on a range of popular internet services.
When the researchers assessed 75 popular services from the Alexa top 150 websites to see if they could be exploited via pre-hijacking attacks, they discovered that at least 35 of them could be exploited using one or more of these methods.
The Unexpired Email Change Attack, for example, has been discovered to be vulnerable to Dropbox. The Trojan Identifier Attack has been discovered to be susceptible on Instagram. The Unexpired Session Attack, as well as a variant of the Trojan Identifier Attack, were both possible targets for Microsoft's LinkedIn. Two of these attacks were discovered to be vulnerable in both WordPress and Zoom.
Sudhodanan and Paverd claim to have responsibly exposed all 56 vulnerabilities they discovered for 35 services, with 19 of them being reported through third-party bug services such as HackerOne, Bugcrowd, and Federacy. They also claimed to have contacted 11 more companies using their security reporting email addresses. The companies that received these reports should, in theory, have addressed them by now.
Related Article : A US College To Shut Down for Good Following a Ransomware Attack









