A security researcher managed to breach Toyota's Global Supplier Preparation Information Management System or GSPIMS through a backdoor. The hacker responsibly reported the breach to the company and published a blog detailing the hack after 90 days.
The Breach
The car company's web application is where suppliers and employees remotely log in to manage Toyota's global supply chain. The security researcher that was able to get into the system goes by the name "EatonWorks," and got into the portal after discovering a backdoor.
It appears that the system allowed anyone to enter an existing account as long as they knew their email, according to Bleeping Computer. Upon breaching, the hacker accessed around 14,000 confidential documents, internal projects, supplier information, and more.
The security researcher reported the issue back on November 3rd of 2022. Toyota fixed the issue by November 23rd. Sadly for the researcher, Toyota did not provide compensation for coming to them with the security breach.
Unlike Toyota, Google rewards users who come forward with an issue that threat actors could exploit. The tech company would give $100,000 to any contributor, which has been proven when a Google Pixel user informed the manufacturer of a way to bypass the phone's security.
The Process of Breaching the Portal
Given that the hacker did not work for Toyota, they had to patch the JavaScript code to get past the login screen. By using the Angular framework, developers can choose who can access certain pages, which will return true or false.

The security researcher found a loophole by patching both the returns true, which then fully unlocked the Angular app. The logout code was then erased so the security researcher would not be redirected to the login page.
Once the patch was applied, the hacker saw that the app loaded and can be browsed. They then tried to find API keys or secret API endpoints and found a JWT web token, which is something a user gets when they log in using an email and a password.
The hacker got a JWT token despite having only provided an email and no password. EatonWorks tried to create an HTTP request to determine if the createJWT endpoint worked. The hacker needed a valid email, which according to EatonWorks, was easy to find.
It's also because of the simplicity of corporate emails from the car maker, with the format "firstname.lastname@toyota.com," and all the security researcher had to do was Google Toyota employees. Upon executing the createJWP HTTP request, it returned a valid JWT.
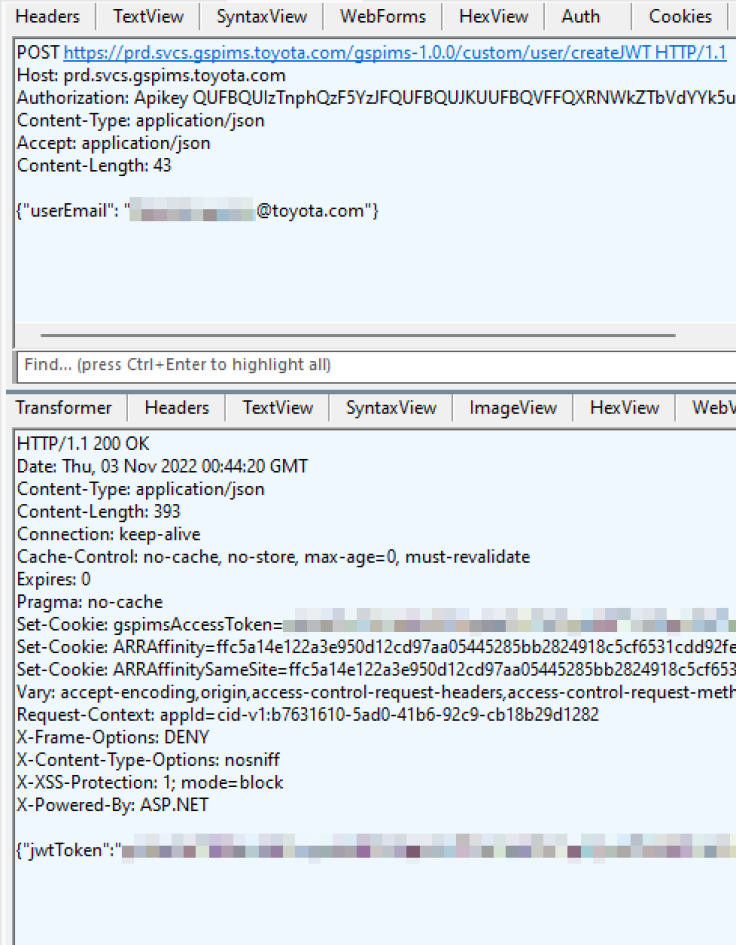
The hacker completely bypassed the corporate login flows, which may or may have not used two-factor authentication as well. Since the portal's API authenticated access via cookies, EatonWorks just added the access token through Chrome's dev tools.
The security researcher found an information disclosure flaw with the API, so EatonWorls used a system admin's email address. This allowed them to gain access to sensitive data like classified documents, project schedules, and the 14,000 user data.









